Modern vehicles are increasingly reliant on sophisticated electronic systems, making them vulnerable to hacking through scanning tools. These tools, originally designed for diagnostics and repairs, can be misused to access and manipulate a vehicle’s network, potentially compromising safety and security. This article delves into the world of Hacking Scanning Tools, exploring their capabilities, the risks they pose, and how car owners and technicians can protect themselves.
Car hacking is no longer a scene from a science fiction movie; it’s a real threat. Understanding how these tools work is the first step in protecting yourself. One resource you may find helpful is information on network scanning & hacking tools.
What are Hacking Scanning Tools?
Hacking scanning tools are software or hardware devices used to identify vulnerabilities in a vehicle’s electronic systems. They can range from simple OBD-II scanners to more sophisticated devices capable of intercepting and modifying CAN bus communication. These tools can be used to access various systems, including engine control, braking, steering, and even entertainment systems.
How Hacking Scanning Tools Work
These tools typically work by connecting to the vehicle’s OBD-II port, a standardized diagnostic interface. They then send and receive data packets to and from the various electronic control units (ECUs) within the vehicle. By analyzing this data, hackers can identify potential weaknesses and exploit them to gain control.
The Risks of Hacking Scanning Tools
The potential risks associated with hacking scanning tools are significant and can range from minor inconveniences to life-threatening situations. Unauthorized access to vehicle systems can allow hackers to:
- Disable safety features: Disabling airbags, anti-lock brakes, or electronic stability control can have catastrophic consequences.
- Control critical systems: Taking control of steering, acceleration, or braking can lead to accidents.
- Steal personal data: Accessing the vehicle’s infotainment system can expose personal information.
- Track vehicle location: GPS data can be used to track the vehicle’s movements.
A vulnerability scanning tool can help identify potential weaknesses in a vehicle’s network. Understanding these vulnerabilities is key to implementing effective countermeasures.
Protecting Your Vehicle from Hacking Scanning Tools
While the threat is real, there are steps you can take to protect your vehicle:
- Be mindful of OBD-II port access: Avoid leaving your OBD-II port exposed. Use a locking cap or install a security device to prevent unauthorized access.
- Keep software updated: Regularly update your vehicle’s software to patch known vulnerabilities.
- Install a vehicle security system: Aftermarket security systems can provide additional layers of protection.
- Be cautious of third-party devices: Be wary of connecting unknown or untrusted devices to your vehicle’s OBD-II port.
 Vehicle Security Measures: OBD Port Protection
Vehicle Security Measures: OBD Port Protection
“Regular software updates are crucial,” says John Smith, Senior Automotive Cybersecurity Engineer at CyberSafe Auto Solutions. “Manufacturers are constantly working to identify and patch vulnerabilities. Staying up-to-date is the best way to protect yourself.”
NIST Scanning Tools and Automotive Security
NIST (National Institute of Standards and Technology) provides valuable resources and tools for cybersecurity, including those relevant to the automotive industry. While not specifically designed for vehicle hacking, some NIST scanning tools can be adapted to assess the security of automotive networks.
Learning about nist scanning tools can provide valuable insights into general network security principles that can be applied to automotive systems.
Using Web Scanning Tools Kali for Vehicle Security Assessments
Kali Linux is a popular penetration testing platform that includes a variety of web scanning tools. While primarily designed for web applications, some of these tools can be useful for assessing the security of vehicle systems that have internet connectivity, such as infotainment systems.
“Think of your car as a connected device,” advises Maria Garcia, Lead Security Consultant at AutoSec Solutions. “Just like your phone or computer, it needs to be protected from cyber threats.”
Port Scanning Tools: Superscan and Automotive Applications
Port scanning tools like Superscan are commonly used to identify open ports on a network. While typically used in IT infrastructure assessments, they can also be applied to vehicle networks to identify potential entry points for hackers. Understanding how port scanning tools superscan work can help automotive security professionals assess the vulnerability of vehicle networks.
“It’s all about layers of security,” explains David Lee, Automotive Security Expert at SecureCar Systems. “By understanding how hackers use these tools, we can develop more effective countermeasures.”
Conclusion
Hacking scanning tools represent a growing threat to vehicle security. Understanding how these tools work, the risks they pose, and the measures you can take to protect yourself is crucial. By staying informed and proactive, car owners and technicians can mitigate the risk of becoming a victim of car hacking. For more information and assistance, contact ScanToolUS at +1 (641) 206-8880 or visit our office at 1615 S Laramie Ave, Cicero, IL 60804, USA. We are here to help you navigate the complexities of automotive security and keep your vehicle safe.
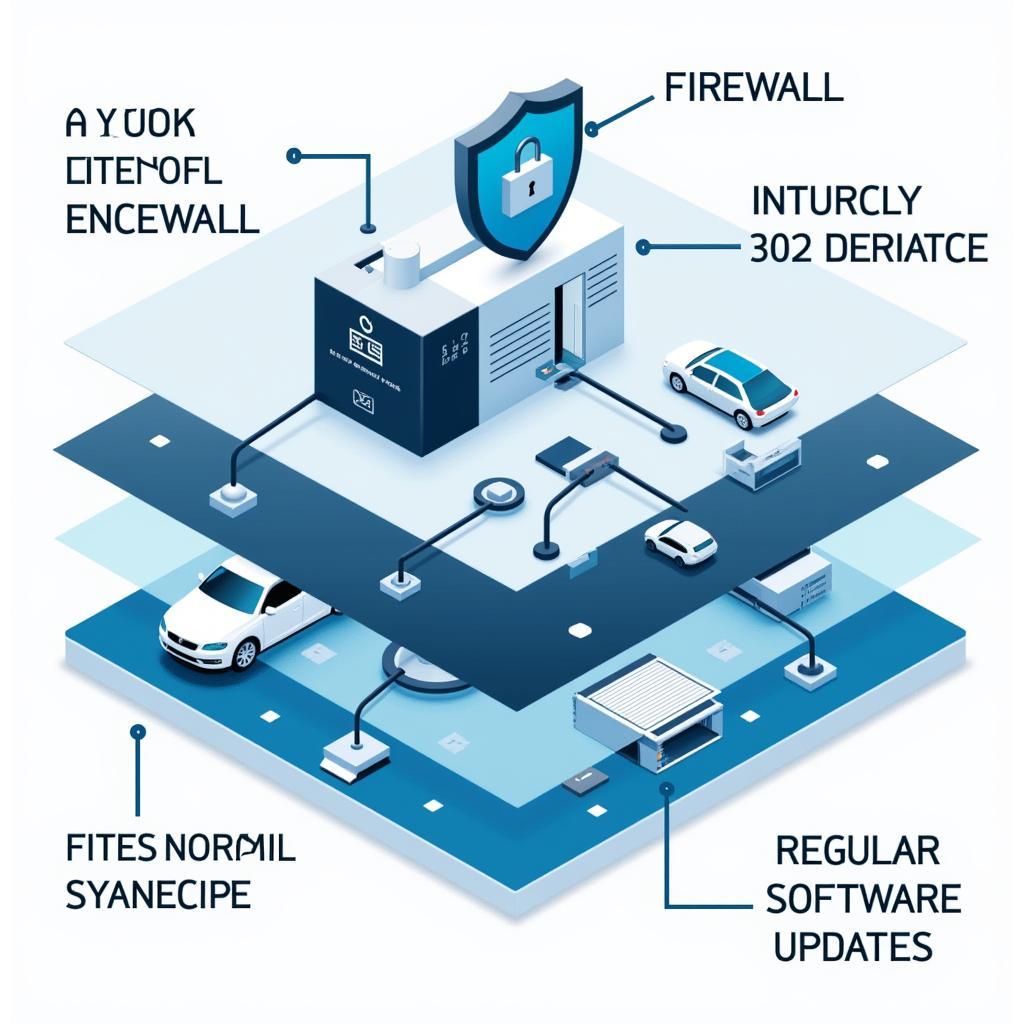 Car Network Security Protection
Car Network Security Protection
FAQ
-
What is the most common entry point for car hackers? The OBD-II port is often the most vulnerable entry point.
-
Can I prevent my car from being hacked? While complete prevention is difficult, taking appropriate security measures significantly reduces the risk.
-
How can I tell if my car has been hacked? Unusual behavior, such as warning lights flashing erratically or unexpected system shutdowns, can be signs of hacking.
-
Are newer cars more vulnerable to hacking than older cars? Newer cars with more complex electronic systems can be more vulnerable, but older cars are not immune.
-
What should I do if I suspect my car has been hacked? Consult a qualified automotive technician or cybersecurity expert immediately.
-
Do insurance companies cover damages caused by car hacking? This is a developing area, and coverage may vary depending on the policy and circumstances.
-
Are there any legal implications for using hacking scanning tools? Using these tools without authorization is illegal and can result in serious consequences. Web scanning tools kali, for example, should be used responsibly and ethically.
