Vulnerability scanning tools aligned with CISAM (Center for Internet Security Automotive and Mobility) are crucial for safeguarding modern vehicles. As vehicles become increasingly interconnected, they present a growing attack surface for cyber threats. Understanding and implementing effective vulnerability scanning is essential for automotive professionals, repair shops, and vehicle owners alike to maintain the security and integrity of these sophisticated systems.
Why CISAM Matters in Automotive Cybersecurity
The increasing complexity of vehicle software and hardware necessitates a standardized approach to security. CISAM provides benchmarks and best practices specifically tailored for the automotive industry, offering a framework for addressing vulnerabilities effectively. CISAM guidelines are not just theoretical; they translate into real-world protection against potential exploits. Utilizing vulnerability scanning tools that adhere to CISAM recommendations ensures a comprehensive and industry-recognized approach to vehicle security. This proactive approach minimizes risks, protects valuable data, and ensures the continued safe operation of vehicles.
Choosing the Right Vulnerability Scanning Tools CISAM Compliant
Selecting the correct vulnerability scanning tools is a critical step in implementing a robust cybersecurity strategy. There are several factors to consider:
- Coverage: The tool should cover a wide range of potential vulnerabilities, including those related to the CAN bus, ECU firmware, and connected mobile devices.
- Accuracy: False positives can waste valuable time and resources. A good tool should minimize these while effectively identifying real threats.
- Ease of Use: The tool should be user-friendly and provide clear, actionable reports. Even for complex scans, the results should be easy to interpret and act upon.
- Integration: Consider how well the tool integrates with existing diagnostic and repair equipment. Seamless integration can streamline workflows and improve efficiency.
- Updates: The automotive cybersecurity landscape is constantly evolving. Choose a tool that receives regular updates to stay ahead of emerging threats.
Implementing Vulnerability Scanning in Your Workflow
Integrating vulnerability scanning into regular maintenance procedures is crucial. This proactive approach allows for early detection and remediation of security flaws, minimizing the risk of exploitation. Here’s a recommended process:
- Vehicle Identification: Accurately identify the vehicle’s make, model, and year to ensure the scanning tool uses the correct vulnerability database.
- Connection: Connect the scanning tool to the vehicle’s OBD-II port or other relevant access points.
- Scan Initiation: Select the appropriate scanning profile based on CISAM recommendations and initiate the scan.
- Report Analysis: Carefully review the generated report, paying close attention to identified vulnerabilities and their severity levels.
- Remediation: Address the identified vulnerabilities by applying necessary patches, updates, or other corrective actions.
- Documentation: Document all findings and remediation steps for future reference and auditing purposes.
Staying Ahead of the Curve: Continuous Monitoring and Updates
The automotive cybersecurity landscape is dynamic. New vulnerabilities are constantly being discovered. Therefore, continuous monitoring and updating of your scanning tools and vehicle software are crucial. This ensures ongoing protection against emerging threats and maintains the vehicle’s security posture.
“Regularly updating your scanning tools and vehicle software is paramount,” says Alex Johnson, Senior Automotive Cybersecurity Engineer at SecureAuto Solutions. “It’s the equivalent of locking your doors at night – a simple yet crucial step in protecting your vehicle from unwanted access.”
The Benefits of Proactive Vulnerability Scanning
Proactive vulnerability scanning offers numerous benefits:
- Enhanced Security: Early detection and remediation of vulnerabilities significantly reduce the risk of successful cyberattacks.
- Improved Safety: Addressing security flaws can prevent potentially dangerous situations, such as unauthorized control of critical vehicle systems.
- Cost Savings: Identifying and fixing vulnerabilities early on can prevent more costly repairs or data breaches down the line.
- Increased Customer Confidence: Demonstrating a commitment to cybersecurity builds trust with customers and enhances your reputation.
 Analyzing Vulnerability Scanning Report
Analyzing Vulnerability Scanning Report
Vulnerability Scanning Tools CISAM: Your Key to Automotive Security
Adopting a proactive approach to cybersecurity is no longer optional; it’s a necessity. By utilizing vulnerability scanning tools aligned with CISAM recommendations, you can effectively safeguard vehicles against evolving cyber threats. This protects both vehicle owners and the integrity of the automotive ecosystem as a whole. Remember, investing in robust cybersecurity measures is an investment in the future of automotive safety and reliability.
For further assistance or to explore our range of diagnostic and repair solutions, please connect with ScanToolUS at +1 (641) 206-8880 or visit our office at 1615 S Laramie Ave, Cicero, IL 60804, USA.
“Investing in the right vulnerability scanning tools isn’t just about protecting data; it’s about protecting lives,” adds Maria Sanchez, Lead Cybersecurity Consultant at CyberAuto Shield. “As vehicles become increasingly connected, the stakes are higher than ever before.”
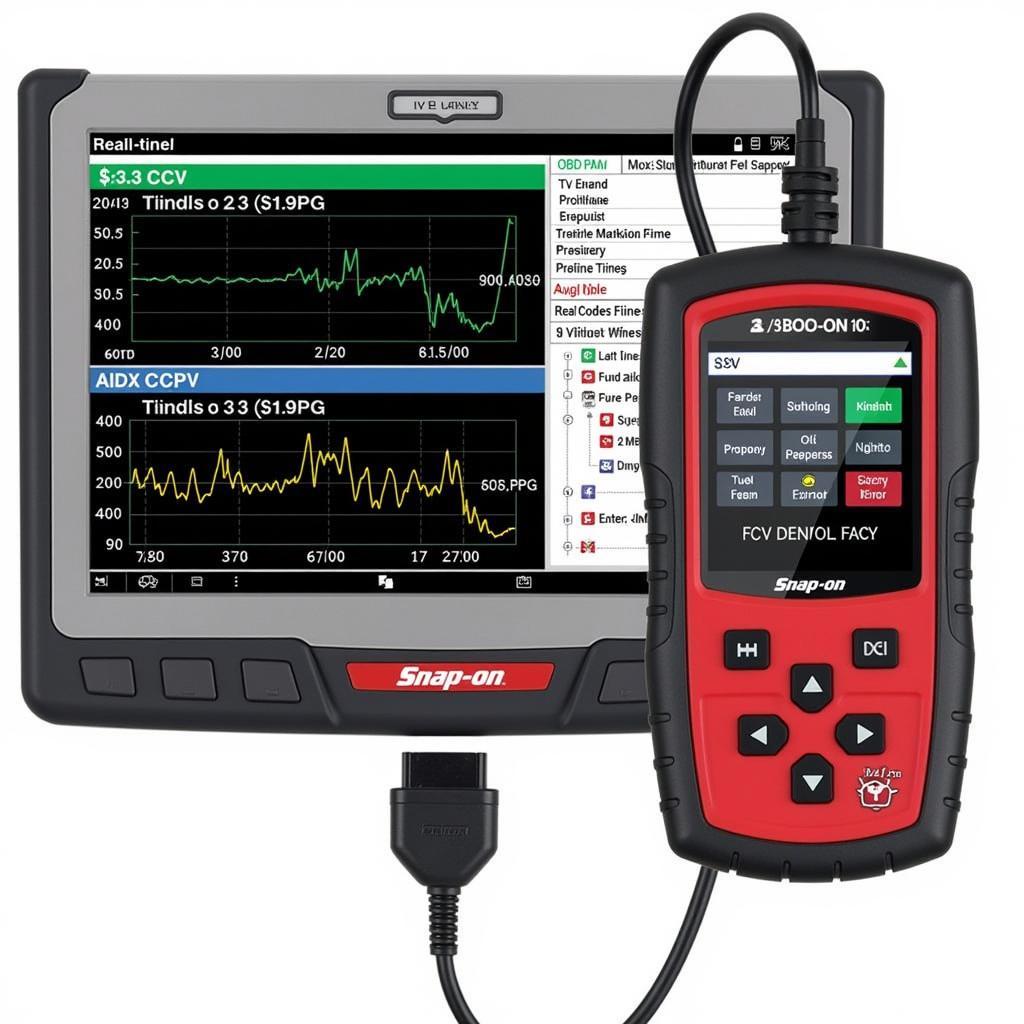
 Connecting OBD-II Scanner for Vulnerability Check
Connecting OBD-II Scanner for Vulnerability Check
FAQ
-
What is CISAM? CISAM stands for Center for Internet Security Automotive and Mobility. It provides security best practices and benchmarks specifically designed for the automotive industry.
-
Why is vulnerability scanning important for cars? Modern vehicles are complex computer systems vulnerable to cyberattacks. Vulnerability scanning helps identify and address these weaknesses.
-
How often should I perform vulnerability scans? Regular scanning, ideally during scheduled maintenance, is recommended.
-
What should I do if a vulnerability is found? Follow the remediation steps recommended by the scanning tool and CISAM guidelines.
-
Are CISAM-compliant tools expensive? A range of tools are available to fit various budgets. The cost of the tool is often offset by the potential savings from preventing costly data breaches or repairs.
-
Can I perform vulnerability scanning myself? While some tools are designed for DIY use, professional assistance is recommended for complex scans and remediation.
-
Where can I learn more about automotive cybersecurity? CISAM and other reputable organizations offer resources and training on automotive cybersecurity best practices.